🗞️ gRPC with Protobuf vs. HTTP with JSON - DevTips Weekly #8
Improving SQL Query Performance, Docker Performance Optimization, Code Refactoring, HTTPS Traffic in Spring Security, and Load Balancing Algorithms
Welcome to another issue of DevTips Weekly (#8)! 📰 This week, I have handpicked articles and resources to keep you at the forefront of technology.
Last week, completely randomly, I read and shared many articles related to ⚡ performance in different fields and aspects, from 🔌 communication protocols performance comparison (gRPC+Protobuf vs. HTTP+JSON) and SQL query performance improvement to 🐳 docker performance optimization. Stay with me to review these articles.
Performance Benchmarking: gRPC+Protobuf vs. HTTP+JSON
The article explores the performance differences between gRPC with Protocol Buffers and HTTP with JSON in a Go-based microservices architecture. The author conducted benchmarks on a local machine, revealing that gRPC outperformed HTTP/2 (H2C) but was slightly slower than HTTP/1. The tests focused on data transport and serialization, avoiding extraneous operations to ensure accurate results. Despite the surprising findings, the structured format of Protocol Buffers over gRPC remains a strong choice for inter-service communication 🚀. The article emphasizes that real-world performance may vary based on hardware and network conditions 🌐.
5 Tips for Improving SQL Query Performance
The article provides 5 practical tips for optimizing SQL query performance. It emphasizes avoiding SELECT * to reduce data processing, using GROUP BY instead of SELECT DISTINCT for efficiency, and limiting query results with the LIMIT clause to speed up performance. It also highlights the importance of using indexes for ⚡ faster data retrieval but cautions against over-indexing, which can degrade write performance. These tips aim to enhance the efficiency and readability of SQL queries, ensuring better application performance.
13 Docker Performance Optimization You Should Know
The article discusses 13 advanced tips for optimizing 🐳 Docker container performance 🚀. It emphasizes the importance of minimizing Docker image sizes, optimizing Dockerfile instructions, and using multi-stage builds to create efficient and secure images 🛠️. The article also highlights the need for efficient dependency management, setting CPU and memory limits, and monitoring container activity to ensure smooth operations 📊. Additionally, it covers disk I/O optimization, preloading Docker images, and using security modules like AppArmor and SELinux for enhanced security 🔒. These strategies aim to improve Docker containers' performance, security, and reliability in various environments.
Code Refactoring: 10 Lessons I Learned About Improving Code
The article emphasizes the importance of code refactoring for maintaining clean and manageable code. It explains that refactoring involves changing how code is written without altering its functionality, making it easier to read and maintain. 🗝️ Key tips include analyzing the code thoroughly before refactoring, collaborating with team members, breaking down complex code into smaller methods, and simplifying conditional expressions. The article also highlights the benefits of incremental changes and balancing readability with performance. Overall, refactoring is presented as a crucial practice for keeping code efficient and ready for future challenges. 🧹💻✨
Accepting Only HTTPS Traffic in Spring Security
The article discusses how to enforce HTTPS-only traffic in a Spring Security-enabled Java web application. By using the requires-channel="https" attribute in the Spring Security configuration, you can automatically redirect HTTP requests to HTTPS. However, this might not be ideal for specific scenarios. To address this, consider allowing HTTP but immediately redirecting to the same URL using HTTPS. Additionally, you can use HTTP Strict Transport Security (HSTS) to instruct browsers to always use HTTPS for future requests, even if the user initially enters an HTTP URL.
System Design Basics - Load Balancing Algorithms
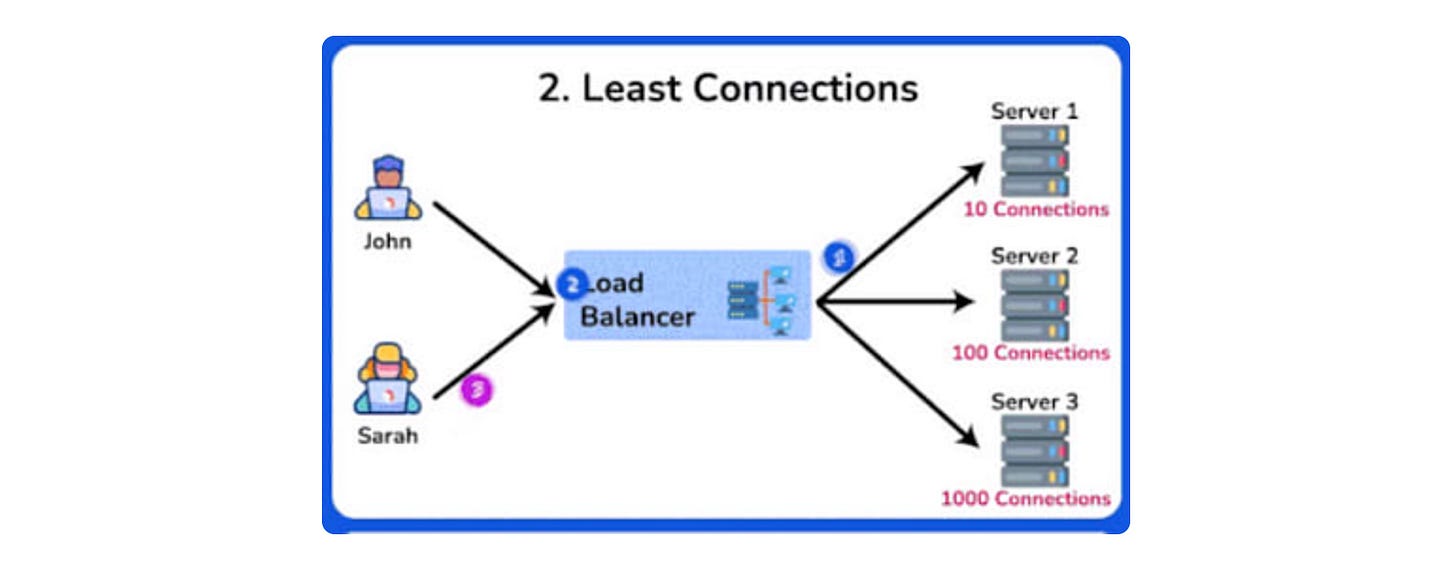
The article discusses load-balancing algorithms 🖥️, which are essential for system design interviews. It covers eight key algorithms: Round Robin, Least Connections, Weighted Round Robin, Weighted Least Connections, IP Hash, Least Response Time, Random, and Least Bandwidth. Each algorithm’s pros and cons are highlighted, along with use cases. The article emphasizes the importance of understanding these algorithms for optimal performance, reliability, and scalability in distributed systems 🌐. It also provides resources for further learning and a free book on distributed system design 📚.
🗞️ Previous issues of the DevTips Weekly
You can also support me in buying a latte ☕️ !(one time or monthly):